The main kudos application logic is designed to be constant[1]. Currently, it includes a signature verification constraint used to authorise receive logics, which might be seen as undesirable since it requires committing to a single signature scheme “forever”.
This post aims to discuss if it is possible and desirable to abstract this signature verification constraint away and how to do that.
What do we mean by authorisation abstraction?
The authorisation constraint we are talking about (in its current form) has two relevant properties:
- It is facing the users. Users provide the signature that is verified in the KL.
- Since KL is assumed to be constant, the chosen signature scheme is also assumed to be fixed.
What makes us not like this arrangement is the lack of choice and flexibility:
- The signature scheme is assumed to be used “forever”
- Users can’t choose the scheme they use to authorise their logic
We want the system to not depend on specific primitives and give the users an opportunity to choose their own security assumptions, so it might sound like a good idea to abstract this constraint away.
Abstracting something away here implies replacing it with some generic constraint bound to a separate constraint verified externally. Roughly, instead of verifying the signature in the KL, we verify a constraint that guarantees that the signature (or whatever way the user prefers) is verified, or, more precisely, that the user authorised the action.
To generalise, authorisation abstraction = replacing a specific authorisation constraint with another more general constraint that guarantees that the removed constraint is verified elsewhere.
AA examples in shielded kudos
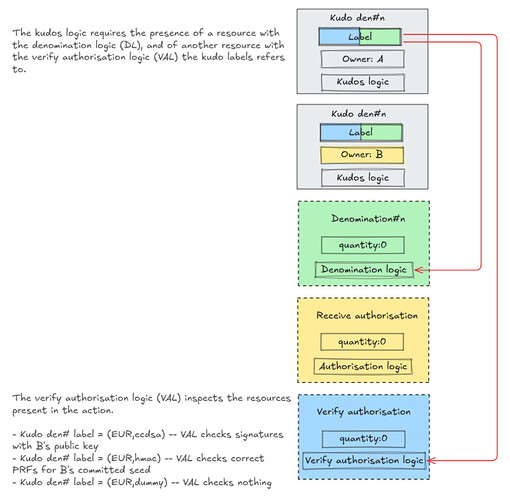
The existing version of the kudos app already have AA:
- KL-DL authorisation abstraction. Instead of having a single logic governing all possible kudos denominations, we abstract away the denomination logic and bind it to the shared KL. The binding mechanism is based on having the same logic for all kudos (KL), including the DL hash in the label and verifying that the relevant logic is present in the same action
- Receive authorisation abstraction. The user can specify their own constraints on receiving in the receive logic. The binding is ensured by signature verification in KL.
Abstraction components
Authorisation abstraction involves three components:
- Ownership mechanism. Currently we express identity using public keys.
- Authorisation constraint carrier. In both existing cases the constraints are carried by resources. In the first case the carrier is a resource of the sub-kind related to the main kind, and in the second case the constraint is carried in a resource of independent kind.
- Verification binding mechanism. We need to make sure that the constraints we are abstracting are verified elsewhere, so that they cannot be substituted by other constraints by a malicious actor. In the first case the binding is done using resource fields, in the second case the binding is done via the signature from the user - externally.
| Internal binding | External binding | |
|---|---|---|
| Independent kind | ? | Receive abstraction |
| Related kind | KL-DL abstraction | ? |
Can we have internal binding for independent kinds?
Independent kinds have different resource logics (otherwise we could express the logics as related). That means we can’t make judgements about the other logic by the fields of the associated resources. The fact that a label/value contains some public key doesn’t imply that this public key is used for anything by this resource.
Can we have external binding for dependent kinds?
In principle, we could, but why, if we can use internal binding, which seems to be always better?
| Internal binding | External binding | |
|---|---|---|
| Independent kind | Receive abstraction | |
| Related kind | KL-DL abstraction |
The current state of the signature constraint
Currently the KL contains a signature verification constraint - external binding for the existing receive abstraction. If we want to abstract the signature away, we essentially want to get rid of the external binding currently hardcoded in KL. At the same time, the authorisation mechanism should ideally be independent of the kudos application: the authorisation logic verifies the external authorisation proof (expressed cryptographically for integrity).
Here are some ways we could try:
- Related kinds + internal binding: in other words, define an authorisation (and possibly the receive logic) kind to be related to the main kudos kind. It would work, but makes not much sense. I don’t like this idea.
- Independent kinds + external binding: replacing a signature over the receive logic with a signature over the authorisation logic that authorises the receive logic. It creates a chain of authorisation logics, doesn’t solve the problem in principle, but does abstract the receive authorisation away. I don’t like this idea either.
- As was suggested at the last cryptography meeting, we can try to change the identity form, in particular switch from public key to a pair (public key, receive logic). I’m going to explore this idea in the rest of the post.
Considered solution: change the form of identity
Let’s imagine that an identity is now expressed as (K_{pub}, L_{recv}). Note that the sender needs to know:
- the value L_{recv} to prove that there is the corresponding resource in the same action
- the value K_{pub} to pass it as private input to the receive logic (for the first constraint)
Where do we currently use ownership:
- KL:
- value encodes the owner of the resource
- KL create constraint: receive logic verification (the constraint we want to abstract) - signature verification.
- DL example:
- kudo label includes the issuer’s identity
- consume constraint for both ephemeral (issuer’s identity) and persistent (owner’s identity) resources - signature verification.
- create constraint for ephemeral resources (issuer’s identity) - signature verification.
- Non-trivial receive logic example:
- label contains the owner’s identity
- create constraint (verify the owner of the kudo against the receive logic owner)
Would the scheme work with the new identity form?
- We can’t use that form of identity in the receive logic label: we introduce a circular dependency. We can use the public key only, but that kind of breaks the definition of identity. Can be acceptable if everything else works.
- The receive logic can’t verify that the kudo is created for the expected user. It can verify the public key, but can’t verify the second component of the new identity L_{recv} - circular dependency.
- Everything seems to be fine with the DL example - we strip the second component of the identity and use the public key to verify signatures.
- The KL constraint issue doesn’t seem to be solved: since the sender knows the components of the identity, they can replace the second component with a simpler logic - we still need to authorise the receive logic.
To summarise, I don’t see how changing the identity form would solve the problem, but I might be missing something. I’m looking forward to see your thoughts.
modulo possibly integrated update mechanisms that are out of scope of this post ↩︎